Strongpoints
- Secure your print fleet
- Configure and control according to your security standards
- Stay compliant with the security standards you have imposed
- Keep your mind at ease and focus on your business!
Description
More than 75% of organizations say they believe security risks have increased significantly in recent years.
Don’t underestimate the power of hackers! With CK Secure, your MFP is at a high level of protection.
« Nobody is going to have fun hacking a printer... »
Not true!
A With the evolution of digitalization and the fact that your printer is connected to your company's network, your printing fleet is equivalent to computers without a keyboard...

With our security offering, we provide your MFP with additional levels of protection.
- Configure and control the products according to your security standards.
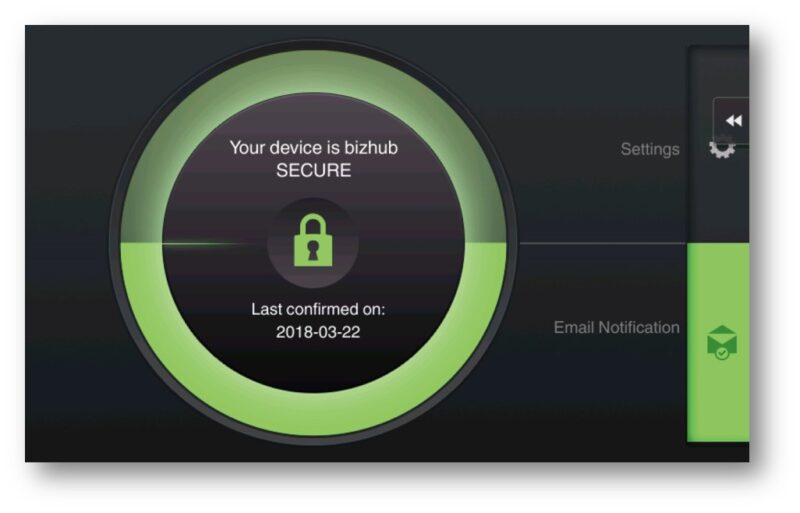
- Relax, our system gives you a visual indication of whether the device complies with the security standards you have imposed.

CK Secure Silver
Change the administrator's password
HDD Encryption
Create a secure alphanumeric password to lock the HDD
Eliminate all traces of data, even after deletions,
with temporary data overwriting.
Program the multifunctional device to automatically delete any material located in electronic folders
Notify KM

CK Secure Gold
CK Secure Silver
+
Disable unsecured and unwanted services, protocols and ports
Enable SSL (self-signed certificate)
Enable network user authentication and automatic logout of user/administrator account
Enable audit logs

CK Secure Platinium
CK Secure Gold
+
Enable real-time scanning
Set up periodic scanning periods
Bit Defender Anti-Virus (LK-116)
Hardware reset
Provision of erasure certificates
Annual verification of security settings
Technology watch (report, white paper, certification, ...)
Possibility to create a customized offer with the options of your choice.

- Reset of the equipment
- Provision of erasure certificates
- Destruction of recording media (HDD, SSD, ...)
- Provision of destruction certificates
- On demand verification of security parameters
- Semi-annual verification of security parameters
- Quarterly verification of security parameters
- Monthly verification of security parameters
- Continuous hardware monitoring
- Installation of PC antivirus software
- Securing the infrastructure
- Technology watch (report, white paper, certification, ...)
- GDPR analysis on office equipment
For more information, contact an expert
See also
Some of our partners


























